Learn the new dimension of Data Loss Prevention
User friendly Interface
Support over 500 applications & keep on growing
Immense protection with ease
Products

Curtain e-locker – a comprehensive Data Loss Prevention system
In everyday operations, users have access to and work on sensitive files. However, it is difficult for companies to control how the users use the files. Once users have access rights to a piece of electronic information, in a sense they “own” the information and as such, they can easily mis-use the information or “leak” the information via different channels (e.g. email, Internet, USB disk, etc). It is difficult for companies to fully control the use of such information. There are many ways by which a user can leak a file.
Curtain e-locker – a DLP – Data Loss Prevention solution, which effectively prevents unauthorized leakage/usage of protected confidential information by any outgoing channels. By using Curtain e-locker, companies can allow authorized users to gain access to confidential files and information. At the same time, the company can also control NOT to allow the users to take the files/information out of the company at their own discretion, like during normal course of daily operations.
Curtain MonGuard – a handy tool to display Screen-watermark
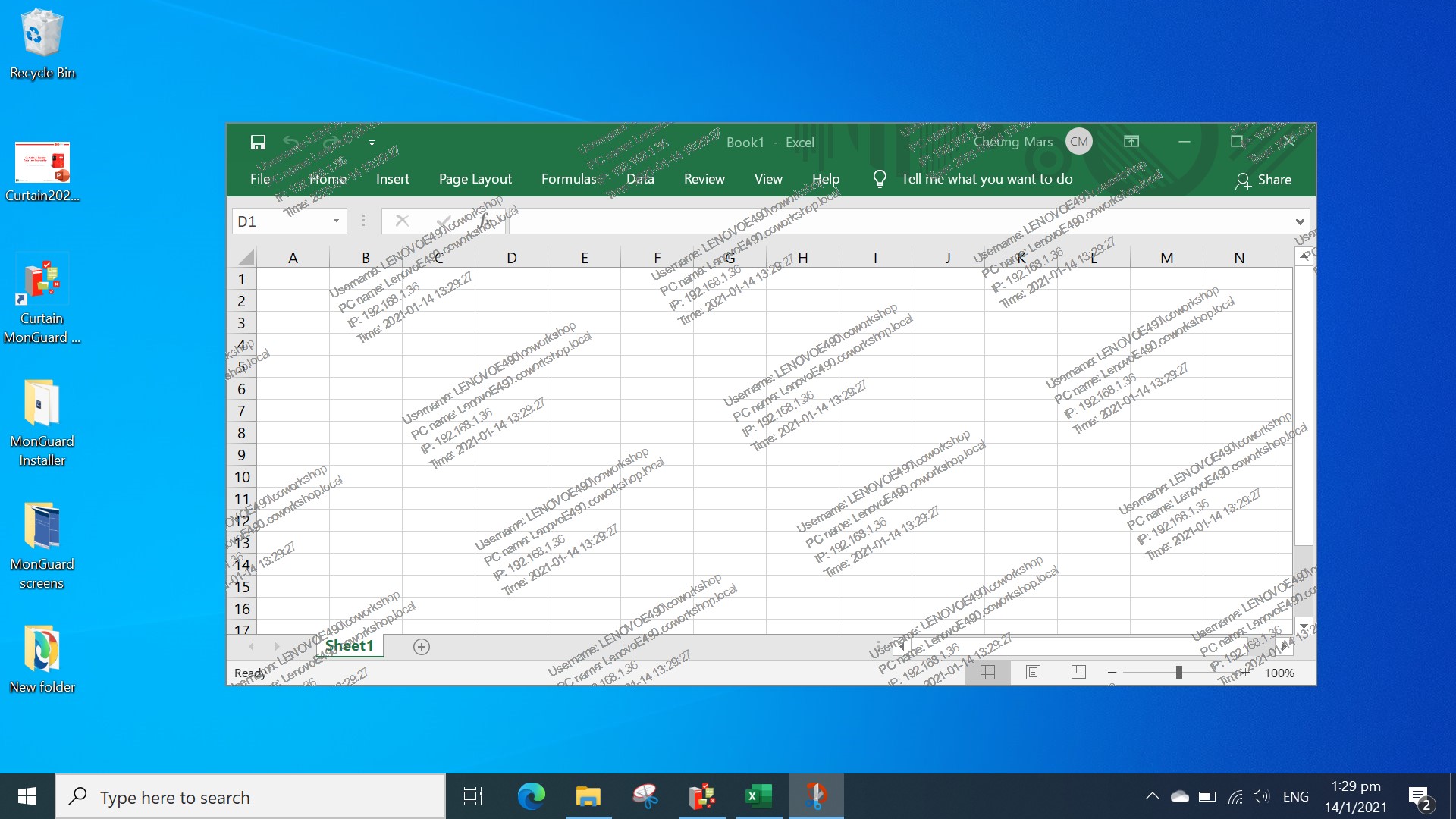
In everyday operations, users have access to and work on sensitive files. However, it is difficult for companies to prevent users taking photo/video against computer’s screen by using mobile phone when accessing sensitive information (e.g. personal information, CCTV footage and other sensitive data). Due to COVID-19, more and more people work from home. Companies have to allow users to download data to notebook and access the data at home or allow them to connect to company’s network through VPN. It increases the difficulty of preventing data leak through screen.
Online meeting is another security challenge. When people need to show something to meeting participants (e.g. contracts, designs and even training materials) during online meeting, how to protect the information shown to participants? Although we cannot prevent people to take photo/video against computer’s screen, at least we should be able to trace the source of data leakage.
Curtain MonGuard allows administrators to display watermark on screen in user’s computers. Since this screen watermark can show user information (e.g. computer name, username and IP address), it effectively gets user’s attention before they capture screen and share the information with other people.

Demo Movies
Other Movies
- How to setup e-locker protection for File Servers (14:26)
- How Curtain e-locker protects SolidWorks EPDM (08:21)
- How to setup e-locker protection for SolidWorks EPDM (15:35)
- How Curtain e-locker protects CCTV (12:35)
- Curtain e-locker Overview Demo (Cantonese 08:17)
- How to setup e-locker protection for File Servers (Cantonese 18:17)
- Visit our YouTube channel for more demo movies
Features
| Curtain e-locker | Curtain MonGuard (FREE) |
Curtain MonGuard (Paid version) |
|
|---|---|---|---|
| Price | |||
| Objective | All-round Data Loss Prevention Solution | Prevent data leak through computer’s screen | Prevent data leak through computer’s screen |
| Control unauthorized saving / printing / sending file out | √ | ||
| Control unauthorized Print Screen / Copy-n-paste | √ | ||
| On-screen watermark | √ | √ | √ |
| Self-defined content of screen-watermark | √ | √ | √ |
|
– Static message |
√ | √ | √ |
|
– Date/Time |
√ | √ | √ |
|
– Computer name |
√ | √ | √ |
|
– Username |
√ | √ | |
|
– IP address |
√ | √ | |
| Full screen-watermark | √ | √ | √ |
| Application screen-watermark | √ | √ | √ |
| Screen-watermark by condition | √ | √ | √ |
| Integration with Active Directory | √ | √ | √ |
| Password management | √ | √ | |
| Uninstall password for client | √ | √ | |
| Self protection for the software | √ | √ | √ |
| Central administration | √ | √ | √ |
| Curtain Admin delegation | √ | √ | |
| Online/Offline Protection | √ | ||
| Secure generation of PDF file | √ | ||
| Secure internal file sharing | √ | ||
| Housekeeping of downloaded files | √ | ||
| File / Print log | √ | ||
| Watermark for printout | √ | ||
| Snapshot for printout | √ | ||
| Approval for sending file out | √ | ||
| Copy-out with declaration | √ | ||
| Local encrypted drive | √ | ||
| Technical support | √ | √ | |
| Software updates | √ | √ |
FAQs
- What is the security challenge for most companies?
- What is the purpose of Curtain e-locker?
- Backend systems (e.g. Windows file server) also have access control. Why do we need Curtain e-locker?
- USB port and Internet access are blocked in my company. Why do we still need Curtain e-locker?
- What is the difference between Curtain e-locker and other solutions in the market?